Proactive Cyber Resilience for PE Firms and Portfolio Companies
How Compello Partners’ vCISO Platform Delivers Tailored Security and Compliance Solutions.
Industry Perspective
Private equity firms and their portfolio companies face heightened risks from cyberattacks due to the sensitive and valuable data they handle. According to a Verizon report, 43% of cyberattacks target small to mid-sized businesses (SMBs) because they often lack robust defenses. Similarly, a Ponemon Institute survey found that 47% of SMBs are uncertain about protecting themselves due to limited expertise and resources. Increasing data protection regulations like GDPR and CCPA add complexity, demanding specialized compliance management.
Private equity-backed businesses must meet higher standards to mitigate risk at fund and portfolio levels but often lack the security expertise required for comprehensive oversight. Relying on internal IT teams or Managed IT Service Providers (MSPs) isn’t always practical, and cybersecurity reports presented to the board may not accurately address fundamental gaps, leaving vulnerabilities exposed.
Business Situation
Portfolio companies often rely on internal IT teams or MSPs to conduct network scans, fill out cyber insurance forms, and generate security reports. However, MSPs can lack crucial security certifications and tend to be reactive. Many companies struggle to understand their risk profile and how best to prioritize security investments. While private equity firms require comprehensive oversight, they don’t want to overwhelm portfolio companies and often lack specialized expertise to monitor risks consistently.
Feedback from operating partners, executives, and deal teams reveals recurring themes like “We care about security,” “It’s top of mind,” and “We have tools in place,” but many admit they could do more. There’s uncertainty around whether the current controls and resources are genuinely adequate. Key challenges at the portfolio level include:
Limited Budgets: Restrict hiring specialized security experts.
Lack of Context: Security tools identify deficiencies but miss the business impact.
Reactive MSPs: MSPs may lack security professionals and focus reactively.
Operational IT: Internal IT teams prioritize maintenance over security.
Risk Awareness: Poor awareness of risk profiles increases exposure.
Oversight Confusion: Companies don’t fully understand the necessary level of security oversight.
Inaccurate Assessments: Incorrect responses to cyber insurance applications heighten risks.
No News Is Good News: A reactive approach leaves security gaps unaddressed.
Overreliance on Assessments: Periodic third-party assessments often miss severity, priority, and risk exposure.
The Solution
A proactive virtual CISO (vCISO) software platform enables private equity firms and their portfolio companies to assess, plan, remediate, manage, and optimize security and compliance:
Tailored Cyber Profiles and Automated Assessments:
Compello Partners builds tailored cyber profiles through questionnaires and surveys and identifies critical vulnerabilities and internal security gaps through scans.
AI-Driven Compliance and Remediation:
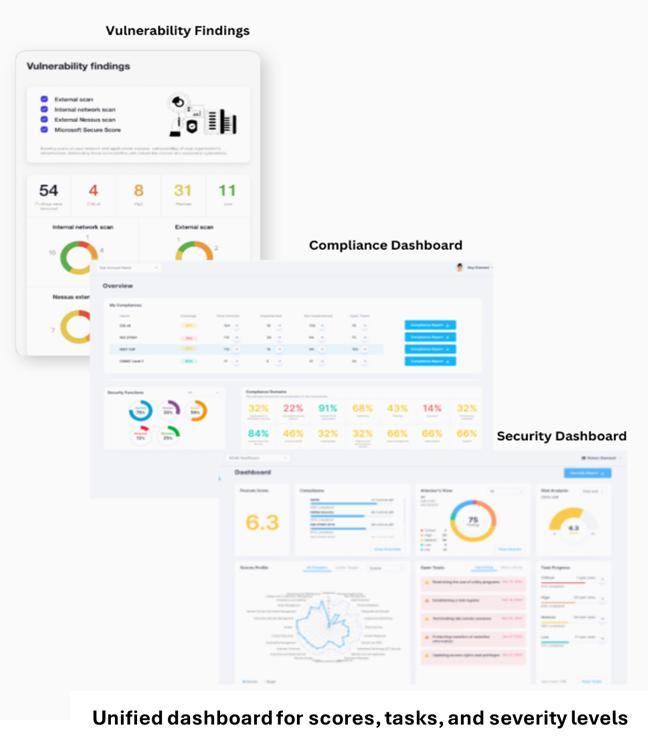
The platform uses AI to automate risk and compliance assessments, creating tailored policies and remediation plans. A real-time dashboard provides gap analysis, compliance status, and client reports, all while managing tasks to drive progress.
NIST-Based Policies:
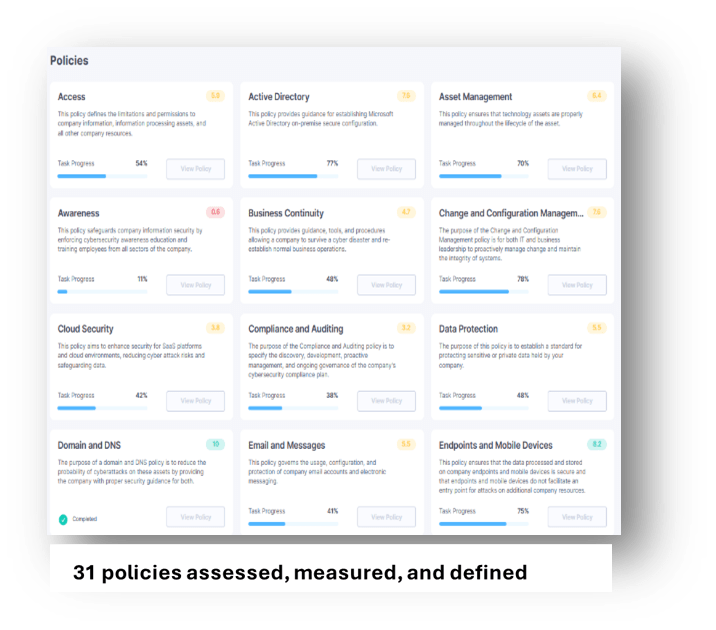
Automatically generated policies are customized to each client’s risk profile, benchmarks, and areas like network security, access, and endpoint security.
Prioritized Task Management:
Proprietary AI algorithms analyze remediation tasks and create a prioritized list, ranging from technical controls to configuring security components.
Advanced Task Management Features:
The platform includes notifications, prioritization for critical tasks, user assignments, and milestone management.

Customized Risk Scoring:
The platform evaluates specific risks, such as ransomware and fraud, and provides a cyber protection score that helps PE firms monitor and address threats.
Customer-Facing Reports:
Branded reports offer stakeholders detailed status updates, highlighting security levels, improvement trends, compliance gaps, and industry comparisons.
Conclusion
By leveraging Compello Partners’ AI-driven vCISO platform, private equity firms gain comprehensive, automated cybersecurity solutions tailored to each client’s risk profile and evolving threat landscape. This ensures strategic cybersecurity management, meeting financial objectives while ensuring regulatory compliance.
1A virtual Chief Information Security Officer (vCISO) is an outsourced security expert or team that helps businesses manage their cybersecurity strategy, risk management, and compliance needs. Unlike a traditional in-house CISO, a vCISO offers flexible, scalable services tailored to each organization’s unique requirements. This approach ensures comprehensive protection without a full-time executive’s cost or resource commitment.
2 The National Institute of Standards and Technology (NIST) is a U.S. federal agency under the Department of Commerce. Its mission is to promote U.S. innovation and industrial competitiveness by advancing measurement science, standards, and technology. In cybersecurity, NIST is known for developing the Cybersecurity Framework (NIST CSF) and other standards, such as NIST 800-53, which organizations use to establish best practices for managing cybersecurity risks. These frameworks provide guidelines for improving critical infrastructure security, safeguarding data, and aligning IT practices with regulatory compliance and industry standards.
Want to learn more?
Click here to schedule a call with a Compello Partners representative.

 synergy identification during mergers and acquisitions, ultimately driving significant value creation and positioning the company for long-term growth and competitive advantage.
synergy identification during mergers and acquisitions, ultimately driving significant value creation and positioning the company for long-term growth and competitive advantage.